Privileged Access Management(PAM)
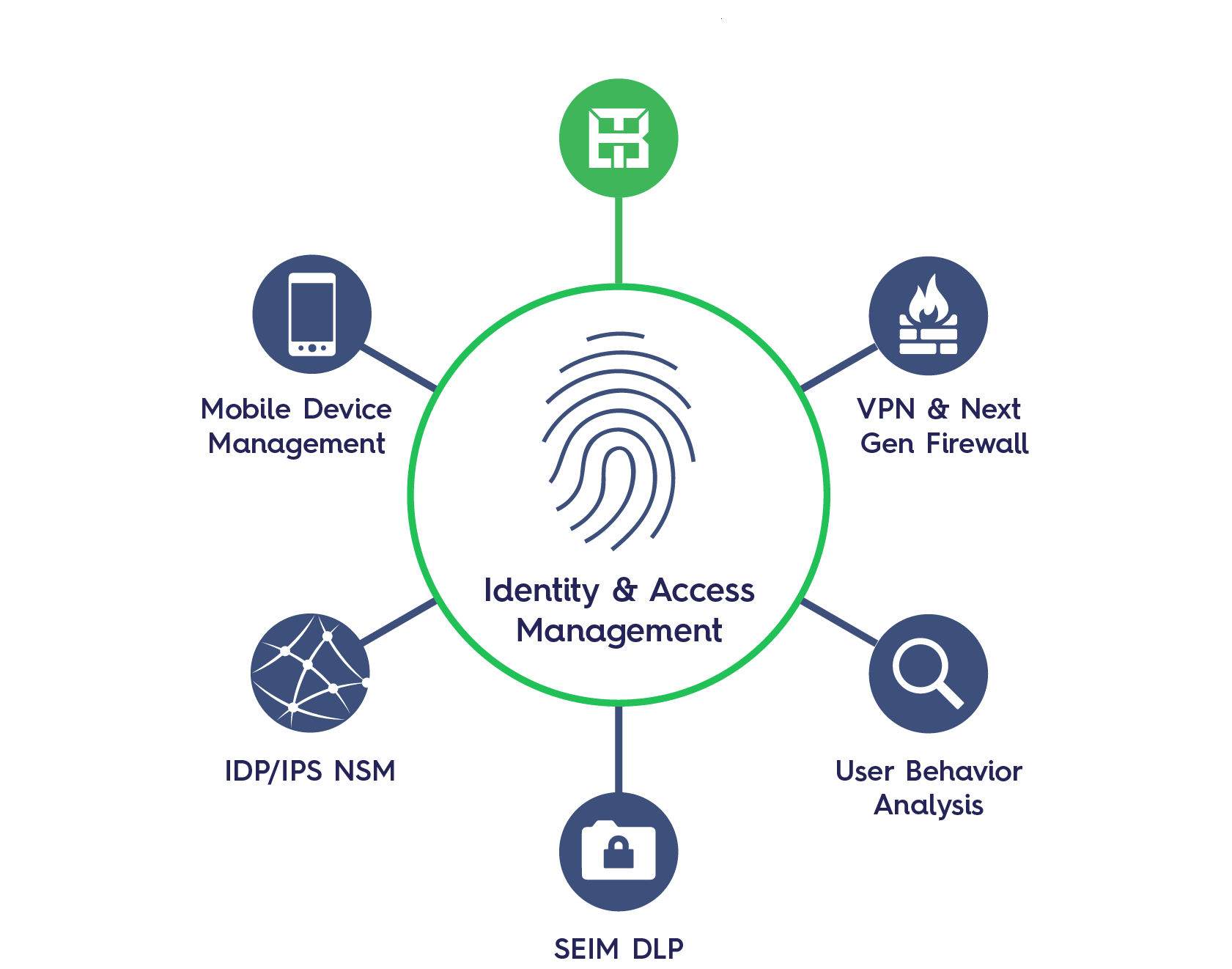
PAM technologies help organizations to provide secured privileged access to critical assets and meet compliance requirements by securing, managing and monitoring privileged accounts and access.
PAM keeps your organization safe from accidental or deliberate misuse of privileged access. This is particularly relevant if your organization is growing. The bigger and more complex your organization’s IT systems get, the more privileged users you have. These include employees, contractors, remote or even automated users. Many organizations have 2-3 times as many privileged users as employees!
Some of these admin users can override existing security protocols. That’s a big vulnerability. If administrators can make unauthorized system changes, access forbidden data, and then hide their actions, you’re in trouble. Insider threats aside, this is a huge opportunity if an outside attacker can gain access using these admin credentials. PAM solves this problem. A PAM solution offers a secure, streamlined way to authorize and monitor all privileged users for all relevant systems.